Alright, so let’s get real for a second—when someone throws the term CUI at you, it might sound like alphabet soup. But trust me, it’s more like the secret sauce to keeping sensitive info safe. CUI stands for Controlled Unclassified Information, and while it may not be “top secret” James Bond-level stuff, it’s still important enough that Uncle Sam wants it locked up tighter than your grandma’s cookie jar.
So what kinda tech setup do you need to handle CUI like a pro? Buckle up, ’cause we’re about to dive deep—but not in a boring, dry-as-toast kind of way. We’re talking firewalls, encryption, and maybe a few coffee-fueled late nights. Let’s go!
🧠 First, What Even Is CUI?
Before we get to the nuts and bolts, let’s clear the fog a bit.
CUI is basically information that’s sensitive—but not classified. Think stuff like:
- Legal documents,
- Technical specs for defense contracts,
- Internal strategy memos.
Now imagine this info falling into the wrong hands—yeah, not great. That’s why the government put together guidelines under frameworks like NIST SP 800-171 and CMMC to make sure businesses and contractors are keeping things secure.
🎯 Why Your System & Network Config Matters
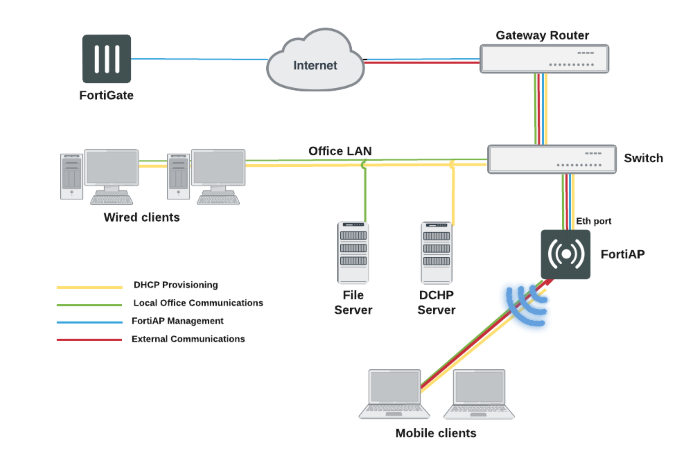
Let me paint a picture: You’re a contractor working on a government project. You’ve got CUI on your laptop. But your Wi-Fi has no password and you’re downloading cat memes from sketchy sites. Yeah… that’s a recipe for disaster.
Your system and network configuration acts like the walls, locks, and alarms around that info. Get it right, and you’re golden. Get it wrong? You might be in breach of compliance—and that can mean fines, legal drama, or losing contracts altogether.
🧰 Core Requirements: What You Actually Need
Alright, here’s the meat and potatoes. According to NIST SP 800-171, here’s what kind of setup you need to keep your CUI safe.
Access Control (AC)
This one’s huge. You can’t just have everyone waltzing in and poking around your files.
- Set up user roles—only authorized folks get access to CUI.
- Use multi-factor authentication (MFA). No excuses.
- Implement session timeouts—if someone walks away from their desk, the system shouldn’t stay logged in forever.
Quick story: One company lost a major contract because an intern got into files they shouldn’t have had access to. Not malicious—just curious. Still cost them big.
Audit & Accountability (AU)
You’ve gotta keep receipts, basically.
- Enable log tracking on all systems that touch CUI.
- Store logs securely for at least 90 days—more if possible.
- Use tools to detect anomalies, like someone downloading too many files at 3AM.
If something shady happens, you’ll want to trace it back like breadcrumbs in a dark forest.
System & Communications Protection (SC)
This is your digital moat. Your firewall. Your electric fence.
- Use encryption—and not the Dollar Store kind. We’re talkin’ FIPS 140-2 validated encryption.
- Segment your network. Put CUI on its own “island” so it doesn’t mix with non-sensitive stuff.
- Block unused ports & protocols. If you’re not using them, they’re just doors waiting to be kicked open.
🖥️ System Configuration: Don’t Just Set It and Forget It
Your systems need to be hardened. And no, that doesn’t mean flexing muscles at your desktop.
🛡️ Secure Baselines
Start with a secure baseline image for every workstation and server. That way, you’re not setting things up from scratch each time—and potentially missing something.
Side note: Ever seen a Windows machine with 43 toolbars installed? Yeah, that’s what happens when you let users go rogue. Lock. It. Down.
🔄 Regular Patching & Updates
It’s tempting to click “remind me later” for software updates, but don’t.
- Enable automatic updates where you can.
- Schedule weekly patch reviews—yes, even if it’s boring.
- Monitor vulnerabilities via CVE databases or tools like Tenable/Nessus.
A single missed patch can be the crack that lets a hacker in. Not worth it.
👥 Least Privilege
Give people the minimum access they need—nothing more. Jan from HR shouldn’t be able to view engineering schematics for a Navy drone. Period.
🌐 Network Configuration: Build a Fort, Not a Shack
Let’s talk about your network—your digital neighborhood. You don’t want it to be the Wild West out there.
🧱 Firewalls & IDS/IPS
You need a firewall. Full stop.
- Use next-gen firewalls with deep packet inspection.
- Deploy Intrusion Detection/Prevention Systems (IDS/IPS) to catch threats mid-sprint.
These tools are like bouncers at the club—only the right packets get in.
🧬 Network Segmentation
Split your network into zones. This way, if someone breaks into one part, they can’t just waltz into everything.
- Use VLANs to isolate traffic.
- Keep CUI environments logically separate from general business operations.
Think of it like putting your valuables in a locked room inside a locked house—extra layers never hurt.
🔐 VPNs & Remote Access
Remote work is awesome. But it’s also risky if not handled right.
- Only allow VPN access with strong encryption and MFA.
- Ban public Wi-Fi unless connected through the VPN.
- Monitor remote sessions for weird behavior—like accessing files at 2AM on a Sunday.
🧪 Testing, Testing… Is This Thing Secure?
It’s not enough to think your setup is safe. You’ve gotta test it like a drill sergeant prepping for boot camp.
🧨 Penetration Testing
Hire ethical hackers to break into your systems—before the real ones do.
- Run annual pen tests.
- Fix the stuff they find. (Seems obvious, but you’d be surprised.)
🔍 Vulnerability Scanning
Use tools like Nessus, OpenVAS, or Qualys to regularly scan for known vulnerabilities.
- Schedule weekly or monthly scans.
- Prioritize high-severity issues and track them to resolution.
🧑🏫 Train Your People (Yes, Really)
You can have the Fort Knox of systems, but if Bob clicks on a phishing email, it’s game over.
📢 Awareness Training
Train your team like it’s a fire drill.
- Teach them how to spot phishing.
- Make them aware of CUI markings and handling procedures.
- Reward good behavior (like reporting a suspicious email)—people love stickers, don’t judge.
True story: A company I worked with had a mandatory “CUI Jeopardy” game every quarter. Silly? Maybe. Effective? Absolutely.
⚖️ Documentation & Compliance
Remember all those fancy configurations? Yeah, you need to document them.
- Keep System Security Plans (SSPs) up to date.
- Record every change in your configuration management system.
- Be ready to show auditors proof that you’re not just winging it.
It’s like taxes—you don’t need to memorize every detail, but you sure as heck need the receipts.
🚧 Common Mistakes (And How to Dodge ‘Em)
❌ “Set it and forget it” mindset
Security isn’t a crockpot. You can’t just turn it on and walk away.
❌ Over-trusting tech without training people
Even the best tools are useless if your team doesn’t know how to use ’em.
❌ Ignoring mobile devices
If employees are checking emails with CUI on their phones, you need mobile device management (MDM).
Alright, I know that was a lot. And if you’re feeling overwhelmed—hey, you’re not alone. The world of CUI compliance is like trying to solve a Rubik’s cube… blindfolded… with one hand.
But here’s the deal: It’s doable.
Start with the basics. Lock down access, segment your network, and train your people. Then build from there. And if you ever feel stuck? Reach out to professionals who eat this stuff for breakfast. Or drop into a forum. Or heck, ask ChatGPT (😉).
Security isn’t a destination—it’s a journey. And while it may not be the sexiest part of your business, it might just be the one that keeps you in business.